


Today, mobile apps are not optional. They are how customers find brands, connect with them, and use their services every day. As a trusted mobile app development company, we build mobile apps that provide smooth, intuitive, and high-performance mobile experiences. Being a native, hybrid, or enterprise mobility provider, we develop apps that are pleasant to work with and provide tangible business value. Having the right combination of creativity, modern tech, and user-friendly design, we assist brands to reach their audience and flourish with confidence in the modern mobile-first world.
Our mobile app developers are fully aware about the new technologies & tools that have been introduced in the market. Having more than 39+ years history of being a top mobile app development service provider, we are assisting companies in launching their own app in the market. Our teamwork culture and working principles have kept us ranked among the top mobile app development companies globally We focus on clean coding, high-end security, and scalability in apps so that they can be modified in the future. Our string development practices are what make us stand out in the crowd. Let's build something amazing together for your business as well!
Using advanced technologies and agile methods, we create high-performance apps for iOS and Android. Our custom mobile app development solutions are mainly focused on user experience and security, ensuring your app is both engaging and safe. Let’s take your idea online.
Want to offer services at your customers’ fingertips? Our on-demand app development brings speed and convenience to life—whether it’s booking a ride, ordering food, or anything in between. We build apps that your users will love.
We develop intuitive, high-performance apps for iPhone and iPad users. From sleek designs to flawless performance, our iOS apps are built to impress and provide smooth experiences on every Apple device.
Great apps need a great design. Our seasoned UI/UX team creates stunning visuals and easy-to-use interfaces, making sure your app not only looks amazing but also works effortlessly for your users.
Reach millions of users on the Android platform with apps that deliver top-notch performance. Our Android apps are built to work perfectly across all devices, giving your users a smooth and enjoyable experience every time.
Why build two apps when you can have one? We develop cross-platform apps that work smoothly on both iOS and Android. Save time, save money, and reach a bigger audience all at once.
Is your app starting to feel outdated? Let’s give it a fresh new look and the latest features. We’ll update your app with the latest UI/UX enhancements, technology upgrades, cloud integration, and security improvements so that it runs better, looks sharper, and keeps up with today’s fast-paced market.
Imagine having an app that combines the best of both web and mobile! We use cutting-edge technologies to create progressive web apps that are custom-built for your business needs. These apps are easy to develop and deploy. It gives you a powerful solution that works seamlessly across all devices.

Get a clear and accurate estimate for your mobile app development requirements. We offer end-to-end mobile app design and development services, helping you understand the scope, timeline, and cost of your project with complete transparency and a well-defined development plan. Let’s have a discussion, as it costs nothing. Later, you can decide if we are a good fit for you or not.
Swift
Objective C
Xcode
UIKit
Java
Kotlin
Android Studio
Android SDK
Kotlin Coroutines
Flutter

React Native
Ionic
NativeScript
Firebase
React
Angular
Redux
With our deep knowledge of the latest app development technologies, our skilled team of developers creates powerful and effective mobile apps. From initial planning and UI/UX designs to the development and launch, we provide complete mobile app development solutions designed around your business objectives and expectations. Even after launching your app in the market, we make sure it works well and is error-free. Our after-service support team better take care of your expectations, and we also want you to be successful in your niche.
Want to connect your devices and systems for smarter operations? Our IoT app development creates apps that link your devices, providing real-time data and improved efficiency. It’s all about making your operations smarter and faster.
Add intelligence to your apps with AI. We can help you build apps that you think are like your users, offering personalized experiences, smart automation, and features like chatbots to keep your users engaged.
Imagine an app that teaches and improves overtime. That’s what we offer with Machine Learning. Our apps analyze data, make smarter suggestions and make better predictions to give your users exactly what they need.
We bring generative AI into your apps to create content, automate tasks, and deliver experiences that feel personal to each user. It helps your app work smarter and faster.
We design voice assistants and chatbots that make your apps easy to interact with. Users can talk or type and get instant answers. This makes your app more engaging and accessible.
We turn your data into actionable insights. Our experts help you forecast trends, understand user behavior, and make informed business decisions. It gives your business a clear advantage.
With proven experience in mobile app development, we help you plan, design, and build mobile apps that align with your business goals. Our team works closely with you throughout the process, maintaining clear communication, high development standards, and on-time delivery at every stage of the project.
Get Expert Guidance
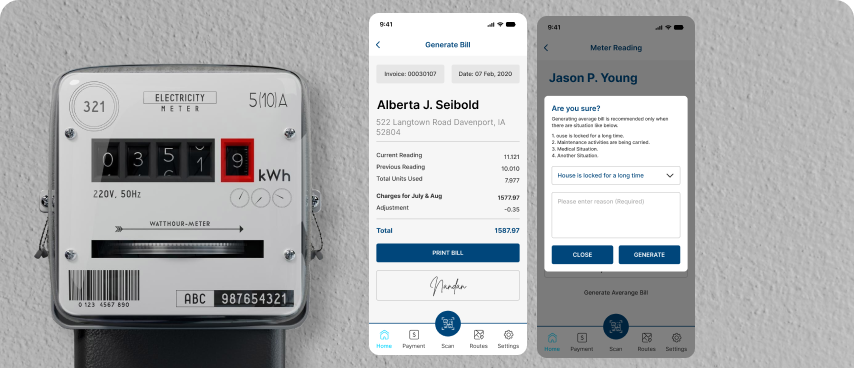
Billing should be quick and hassle-free, especially for field agents handling customer transactions on the go. We developed a smart billing app for a gas utility company that enables their agents to take real-time meter readings and generate accurate bills instantly. This eliminates paperwork, reduces billing errors, and speeds up payments. The app also integrates with backend systems to ensure seamless data syncing, making the entire billing process more efficient.
Explore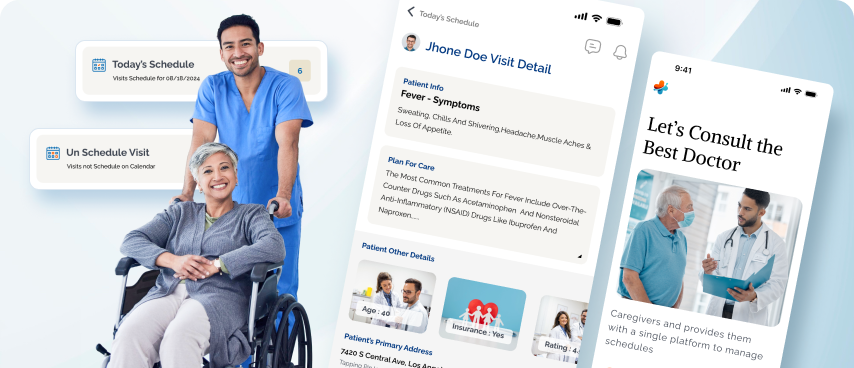
Caring for patients requires careful coordination, and we made it easier with a caregiver app designed for healthcare professionals. It allows caregivers to schedule visits, track patient conditions, set reminders, and manage tasks effortlessly. The app ensures timely care by sending real-time updates and alerts, helping caregivers focus on their patients rather than paperwork.
Explore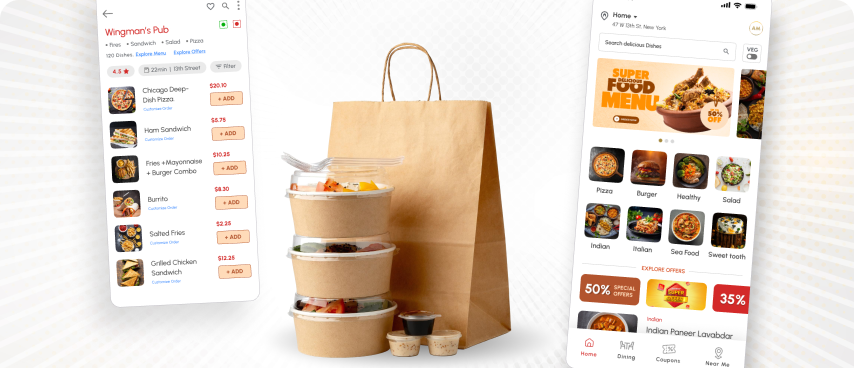
We helped a restaurant chain transform its food delivery operations with a custom-built app that ensures a seamless experience for both customers and restaurant owners. The app features real-time order tracking, easy menu navigation, secure payments, and smart order management. Customers can place orders in just a few taps, while restaurant staff can efficiently handle incoming orders, optimize deliveries, and improve customer satisfaction.
ExplorePeople want to stay fit, but keeping track of workouts and progress can be challenging. That’s why we developed a fitness and activity tracking app that provides users with customized workout plans, step counting, heart rate monitoring, and real-time progress tracking. The app uses AI to suggest workouts based on individual fitness levels and goals, keeping users motivated.
Explore
Travel planning can be stressful, but our AI-powered travel app makes it simple. It helps users find destinations, plan itineraries, and get personalized recommendations. The app can suggest flights, hotels, and activities based on user preferences. It also provides real-time updates and alerts to make every trip smooth and enjoyable. Our team ensures the app is easy to use and reliable for travelers everywhere.
Explore
We built an AI-powered pose detection app for one of our clients to help users track movements and improve performance. The app analyzes body posture in real time, giving instant feedback for workouts, yoga, or rehabilitation exercises. It helps users stay safe, improve their technique, and achieve their fitness or therapy goals effectively.
ExploreDiscover the diverse range of industries we proudly support with our innovative software solutions to companies of different business verticals. Our expertise spans multiple sectors, ensuring tailored services for every unique need.
Various types of mobile apps can be categorized based on industries, technologies, and functionalities. From a technology perspective, different types of mobile apps are native apps, hybrid apps, cross-platform apps, and progressive web apps.
Mobile app helps businesses strengthen the customer relationship, deliver more personalized user experience, and increase brand awareness and customer engagement.
The cost of mobile app development significantly depends on requirements, resources, platforms, locations, time involved, and the complexity of an app.
We offer mobile app development for iOS and Android platforms. We use languages such as Swift, Java, and Kotlin and frameworks such as React Native, Flutter, Ionic, and Firebase to develop native and cross-platform mobile apps.
Yes, we do help our clients submit and publish apps to the App Store – Google Play Store and Apple App Store.
You can hire mobile app developers from mobile app development companies and agencies that have dedicated development team models. You can hire a dedicated app developer from SPEC INDIA through our flexible hiring models to work on your next project idea.
SPEC House, Parth Complex, Near Swastik Cross Roads, Navarangpura, Ahmedabad 380009, INDIA.

This website uses cookies to ensure you get the best experience on our website. Read Spec India’s Privacy Policy