 One tree
One tree One life


Digital transformation has become a strategic necessity. With real-time payments and AI-backed prediction, businesses manage, track, and analyze finances in...

There are billions of sports fans hooked on their mobile devices, who are not only watching but also playing. Fantasy...
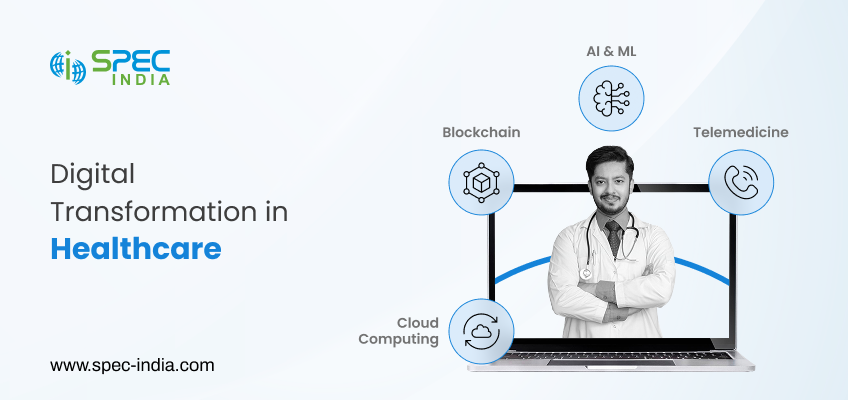
Outdated systems. Siloed data. Long wait times. These are some of the bottlenecks that the healthcare providers are still struggling...

Back in 2014, there were 1 billion smartphone users. Now, the number is nearly 4.69 billion and is forecasted to...
Have you ever been so busy with the information your business creates every day? Someone else is going through the...
Healthcare is one of the most significant data contributors. It collects vast amounts of data related to patients, diseases, and...
“SPEC House”, Parth Complex, Near Swastik Cross Roads, Navarangpura, Ahmedabad 380009, INDIA.
“SPEC Partner”, 350 Grove Street, Bridgewater, NJ 08807, United States.
This website uses cookies to ensure you get the best experience on our website. Learn more